This post is part of the FAIR and CTI related blog posts; an event back in January made me want to add this to the mix.
I was interviewing for a Cyber Threat Intelligence Manager position, and part of the interview process was to talk to the person doing intelligence for the Physical Threat Intelligence space. During the interview, I asked which Intelligence models they used in case I had to brush up on one or learn something new. Part of the role was sharing data between the two intelligence groups. Even though the interviewer previously worked in Military Intelligence, they said they didn’t know what I was talking about.
That gave me pause because I went to a DoD-backed program in Undergrad, and we learned multiple Intelligence Processes/Models. I covered them in most of my Threat intelligence presentations and when I was teaching at the same DoD-backed program after I got my master’s degrees. Even after walking through the three, I knew the best; the person I was talking to didn’t know what I was talking about.
So, as I said, I thought I’d go through them into here, for people that haven’t been exposed to them yet. I’ve always figured people reading my blog would be familiar with at least a couple of the models.
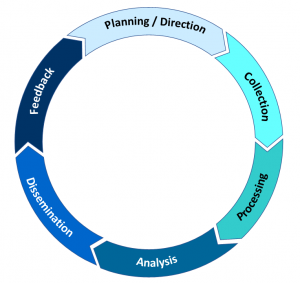
The first one, and I personally use a modified version of it putting feedback in at each step of the cycle, is the Traditional or Classic Intelligence Cycle.
As depicted above, it is a cycle that starts with the Intelligence stakeholder’s question. From there, planning and direction on how to answer the question is formulated. The next step is Collection, where the raw data (individual facts) is collected, which might help answer the question. The third step is to process the collected data into information. It can be through translation, decoding/decryption, re-writing it into a useable state, etc. After processing everything into a usable/readable format, the next step is to analyze the information to make it actionable to the stakeholder(s)—the actual generation of Intelligence. Step five is to share the intelligence, usually a product like a report or presentation. Finally, elicit feedback from the stakeholders to make sure their original question that started the process was sufficiently answered. I’ve personally always found the feedback section the hardest, and more than once felt like I wrote a product that wasn’t read or understood.
As I said above, I like the Traditional process because it’s straightforward. However, I think that there needs to be a feedback loop at each step, especially if the steps are broken across teams, to make sure things are staying on track.
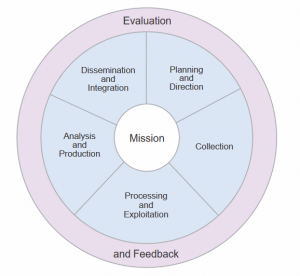
The second model I know is the JP 2.0 “Mission-Centric” process, or what the Joint Intelligence document calls “The Intelligence Process.”
The same elements from the Traditional Intelligence Cycles are there, but this process tries to focus on the Mission while looking at each stage of the Cycle. I tend to think of it as a “built-in” feedback loop asking does what I have done here helps answer what the stakeholder(s) was looking for.
The last one I’m familiar with is Robert M. Clark’s Target Centric process. This model is built around the Target instead of the Mission.
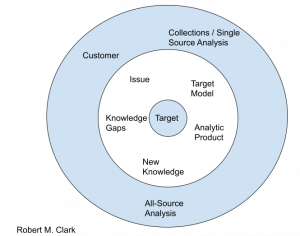
Based on Richard Clark’s process. I used Google Drawings a few years ago to remake what he had in his book.
Clark has an excellent book on the topic. I have the 3rd through 6th editions on my bookshelf. We used the 3rd edition in my Intelligence I class, and I kept up with the new versions after, and I used the 6th edition when I taught the Intelligence I class.
Oh, and I said that event was in January. The delay in getting blog posts written and out is that I got a new job that’s been keeping me busy. No, not the one I talked about interviewing for here. I got a Security Operations Center Manager role at a different company. Maybe I’ll write about it in the future.