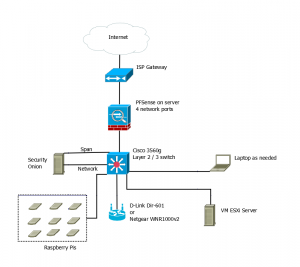
Over the last few weeks I’ve been thinking of redoing my iptables, but by putting in a default deny rule, does that make us bad netizens? By dropping everything that isn’t allowed, it actually makes it harder to fix the original problem. The fact that there are attacks to begin with, and the fact that boxes are compromised.
Over the last few months, since fixing the IMAPS part of my mail server, I noticed people hitting the server and failing to log in. These were not targeted attacks; they were automated bots, using the same users and possible passwords. I’d block them at the firewall but every day, there would be at least 2 new networks. Not all of them from overseas.
For historical reasons I take a stance of contacting the abuse email for North American companies, and some European ones. I found that the large Cable Company ISPs, usually turn out to be black holes. The smaller ones though actually reply back.
Last week I went through a week’s worth of logs, and out of the 47 ip addresses, there were about 30 networks. I actually sent 17 emails, and blocked only 13 networks. From that, 9 replied. Granted they were mostly the auto-replys, but I did have 2 that were interesting. One was from an ISP in England and they thanked me for letting them know. The other was an educational ISP in California. They replied back where they found the problem, and the IR procedures, with a thank you.
That worked because I wasn’t blocking the inbound connections, and letting other tools protect the server’s processes. However the iptable rules had become larger than I wanted to maintain (over 100) for inbound access. So I re-wrote them using a default deny. I now state what on my network can be talked to, and in some cases by what networks. Everything else gets dropped and logged.
The down side to this is that while I can see the dropped connection attempts, I can’t see what the people are trying to do. Is it just a null hit, a failed loggin attempt, something else. I also can’t report it back to other interested parties. While I feel better about their failures, I realize that I’m a bad Netizen because I can’t contact their upstream, with logs showing the problem.
Yes, I know I could set up a honey pot system and fight for both the user and the internet that way, but it feels more like just being the complaint department than it does trying to solve things.
While I am going to keep using the default deny, because it’s easier to handle the rules on the firewall, I still don’t like that I’m walling myself off from the real problem, and not trying to fix underlying issue.